TRANSFER CHILD SUPPORT CASE FROM TX TO FLORIDA
TRANSFER CHILD SUPPORT CASE FROM TX TO FLORIDA Here are the key steps to transfer a child support case from Texas to Florida: File a

ChatGPT4 FEATURES With ChatGPT4, you’ll be able to communicate with natural language processing like never
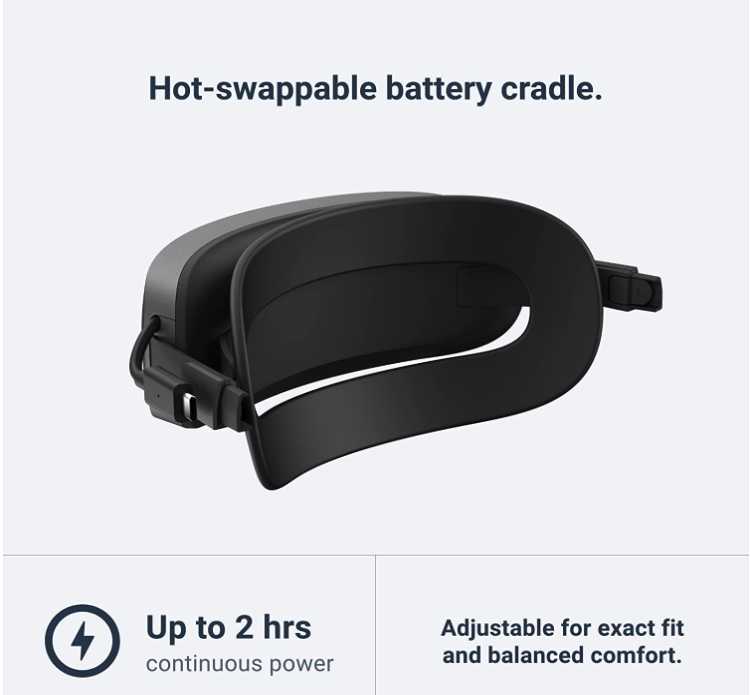
THE TOP VR HEADSETS OF 2023 The Top VR Headsets of 2023: A Comprehensive Guide
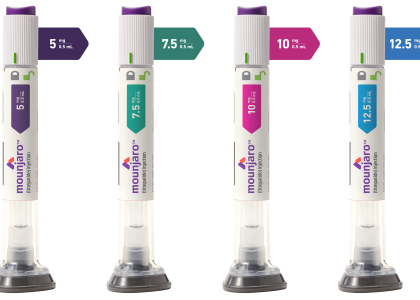
MOUNJARO WEIGHT LOSS Introduction Mounjaro Weight Loss is a revolutionary weight loss program that has

BREAKDOWN HOW TO CREATE THE BEST AI PROMPTS Unlock the Power of AI with Breakdown’s

AI PROMPTS Mid-Journey Prompts play a crucial role in maintaining customer engagement and driving conversions.